Crisis Mode Activated:Simulating a Breach to Secure the Frontlines
Text to Speech in Multiple Languages
In May 2024, the UK Ministry of Defence (MoD) faced a significant data breach that exposed the personal information of over 225,000 military personnel [1]. This incident, involving a third-party contractor's system, has raised serious concerns about third-party vulnerabilities and the potential for state-sponsored cyberattacks.
The Breach Details:
In early May 2024, the MoD discovered that a third-party contractor’s payroll system, used for managing the armed forces' payment network, had been compromised [2][3]. The breach exposed sensitive data, including names, bank details, and in some cases, addresses of current, reserve, and some former military personnel [4][5]. The system was separate from the MoD’s core network, emphasizing the risks of external dependencies [6]. The MoD took immediate action by isolating the affected system and launching an investigation, describing the incident as the work of a "malign actor," with speculation pointing towards state involvement, though no specific country was named [1][7].
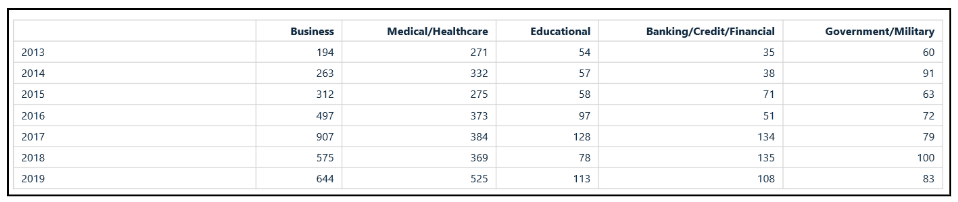
Research suggests that government sectors, including defense, have seen a rising trend in data breaches, with the U.S. reporting over 1,000 breaches from 2005 to 2024, highlighting the sector's vulnerability [8]. Technically, the breach likely involved unauthorized access through a vulnerability in the contractor’s system, possibly exploiting weak authentication mechanisms or unpatched software, which allowed the attacker to exfiltrate data over an extended period before detection.
Third-Party Risk and Defense Agencies:
This breach highlights the critical importance of managing third-party risks in the defense sector. Defense agencies often rely on external contractors for services like payroll management, but these partnerships can introduce security vulnerabilities if the contractors’ cybersecurity measures are inadequate. The UK MoD’s experience shows that even when internal systems are secure, data can still be compromised through third-party systems handling sensitive information, likely due to a failure in the contractor’s security protocols. From a technical perspective, this could involve inadequate network segmentation, lack of endpoint security, or insufficient logging and monitoring, allowing attackers to move laterally within the contractor’s environment.
Statista data indicates that in 2023, the government sector, including defense, accounted for a significant share of data breaches in the U.S., at around 15%, underscoring the need for robust third-party security [9].
Lessons for Defense Agencies:
This incident offers several key lessons for defense agencies worldwide, with technical implications:
- Third-Party Risk Management: Regularly assess and monitor the cybersecurity practices of all third-party contractors handling sensitive data, ensuring they implement strong network security measures like firewalls, intrusion detection systems, and regular vulnerability scans.
- Data Minimization: Ensure that only necessary data is stored and that access controls are strictly enforced, using techniques like role-based access control (RBAC) and data encryption at rest and in transit.
- Incident Response Planning: Develop robust incident response plans with clear communication strategies and protocols for isolating affected systems, leveraging tools like security information and event management (SIEM) systems for real-time alerts.
- Employee Training: Educate personnel on cybersecurity best practices and the importance of reporting suspicious activities, including phishing awareness and secure handling of third-party communications.
Simulating the Breach with CRISISIM™:
CRISISIM™ is a real-time scenario simulation tool designed to help organizations practice responding to cyber incidents. By simulating a scenario based on the UK MoD’s breach, defense agencies can test their ability to detect and respond to unauthorized access in third-party systems, practice containment and recovery procedures, evaluate communication strategies with affected personnel and the public, and identify gaps in their current security measures and incident response plans. Through the simulation, defense agencies can enhance their preparedness and resilience against similar cyber threats, especially given the rising trend of breaches in the government sector as shown by Statista data [8].
Conclusion:
The UK MoD’s data breach in May 2024 is a stark reminder of the evolving cyber threat landscape and the need for continuous improvement in cybersecurity practices, especially in managing third-party risks. By learning from this incident and utilizing CRISISIM™ to simulate and train for such scenarios, defense agencies can better protect their personnel and national security interests, particularly in light of the sector’s vulnerability to data breaches as evidenced by recent statistics [9]. The technical insights from this breach, such as the importance of network segmentation and endpoint security, can be directly applied in simulations to build a more resilient defense against future attacks.
References:
- New York Times article on UK armed forces data breach
- World Economic forum story on UK military data breach
- BBC news on MoD data breach
- The Guardian article on UK military personnel data hacked
- Massive data breach exposes UK military personnel's paycheck information
- Bleeping Computer article on UK MoD payroll data breach
- MoD data breach: UK armed forces' personal details accessed in hack
- Number of data breaches in the government sector in the United States from 2005 to 2024
- Share of data breaches in the United States in 2023, by industry