Choosing the Right Cyber Range Tailoring Need-based Environments
Text to Speech in Multiple Languages
In our previous blog, we discussed how the journey from traditional cyber ranges to the modern-day/next-gen cyber range represents a significant paradigm shift. Traditionally, large organizations, both military and commercial, grappled with the challenges of expensive virtual environments, making them less accessible for widespread adoption. However, recognizing the pivotal need for a last line of defense and the evolving role of Security Operation Centre (SOC) analysts and incident response professionals, the traditional cyber range has metamorphosed into a dynamic and tailored next-gen counterpart.
In this blog, we will delve into the intricacies of cyber range types, which can vary depending on the needs of the user or the number of users it can support. They can also vary in terms of capabilities, like what kind of training or exercises can they support. Muhammad Mudassar Yamin, Basel Katt, & Vasileios Gkioulos in their research paper Cyber Ranges and Security Testbeds: Scenarios, Functions, tools, and Architecture has proposed an initial taxonomy to classify cyber ranges diagrammatically, including the Purple Team as per the modified taxonomy.
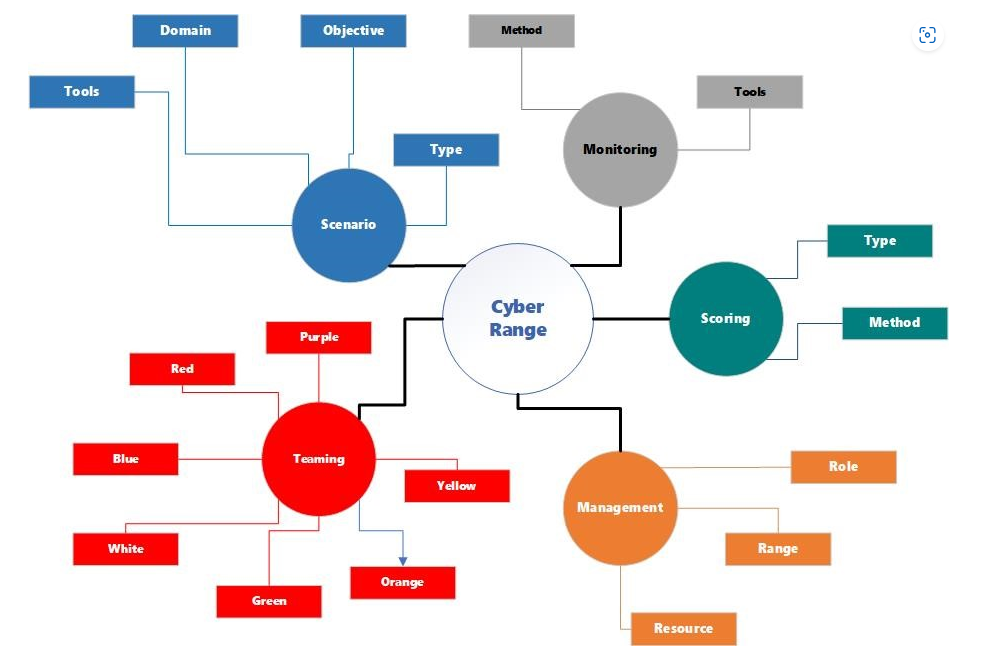 Cyber ranges can either be simulated or emulated environments and can share many similarities of use cases to assist in developing individuals’ skills and knowledge and arranging competitions and exercises for individuals or groups of people from one or more organizations or companies or countries. Cyber ranges could be static during an event, but they may include moving targets.
Cyber ranges can either be simulated or emulated environments and can share many similarities of use cases to assist in developing individuals’ skills and knowledge and arranging competitions and exercises for individuals or groups of people from one or more organizations or companies or countries. Cyber ranges could be static during an event, but they may include moving targets.
We can identify the three types of cyber ranges as follows:
- Physical Cyber Range: As the name suggests, it is a physical cyber range. Users create a test bed of a network or computing infrastructure and often use real components of the reference infrastructure. This typology is one of the best for gaining experience and gathering results to improve the defenses of a given infrastructure. The major disadvantage it has is being less flexible as any modification would require recreating a new cyber range along with including the cost of infrastructure and being very expensive. It is very difficult to find examples of test beds concerning the real-world target infrastructure because of the difficulty of implementation and because creating such structures requires disclosure of business secrets etc.
- Virtual Cyber Range: Everything here is simulated in a virtual environment using virtualization technologies and obtaining test beds of different complexity. The main advantage here is that the components needed to build it can be found easily and that too at a relatively low cost. One can aim to get a higher degree of flexibility with scalability in the ever-dynamic simulated environment. However, the major drawback of it is that the user would not get an experience very similar to the real one.
- Hybrid Cyber Range: These are also known as ‘Cyber-Physical Ranges’. Here, the topology is a hybrid of Physical and Virtual cyber ranges. It combines the positive aspects of both approaches and provides the flexibility of a virtual environment and a new real environment resulting from the use of real-world hardware components.
- There can be ‘Specialized Cyber Ranges’ too. These specialized cyber ranges can be based on the use cases, events, capabilities, or capacity. The technical aspects governing them would be computing power, memory, hard disk capacity, network topology, operating systems, and applications. As an example, a cyber range may require the person to be physically present and may just have a limited number of people allowed to participate as compared to another one, which may allow remote access to its users. A highly specialized "small" cyber range could cope with a modest capacity and capability, but for a large and realistic environment, one may require considerable investments in terms of hardware and software licenses to be able to provide a near-realistic training or exercise environment.
You could also have situations where you could interconnect multiple cyber ranges. One of the key advantages of this would be reduced costs, more scenarios to work on, and larger team interactions, one could easily see which cyber range offers the end user to meet their goals or what cyber ranges can be interconnected to meet the overall goal.
One should note that for interconnection between cyber ranges, one should evaluate interoperability and internet connectivity.Depending on the objective, one can choose a cyber range meeting their requirement. As we unravel the nuanced taxonomy of cyber ranges, the journey continues to the crucial decision of choosing a cyber range aligned with specific objectives. The subsequent exploration will delve into understanding the teams that play pivotal roles within these cyber environments, shaping the landscape of cybersecurity preparedness.