Research Report: Life360 Data Breach Incident
Text to Speech in Multiple Languages
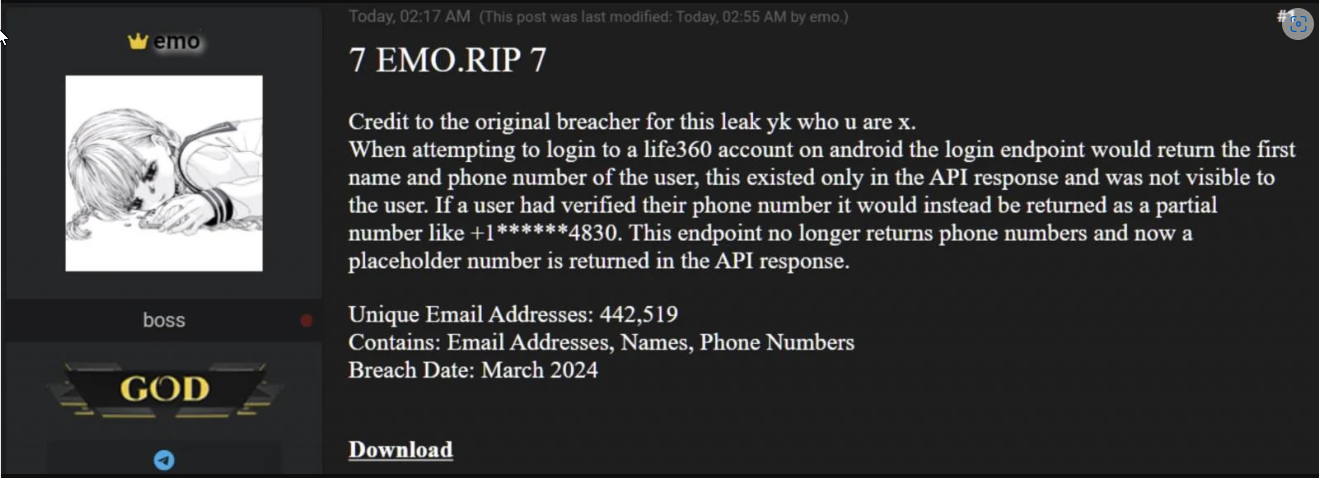
In March 2024, Life360 experienced a significant data breach that exposed the personal information of 442,519 customers. A threat actor, known as 'emo', exploited a vulnerability in the Life360 login API to collect this data. This report provides an in-depth analysis of the incident, including the exploit method, root cause analysis, and conclusions with recommendations for preventing future incidents.
2. Incident Overview
2.1 Breach Details
The attacker exploited an unsecured API endpoint in the Life360 login system, which allowed them to retrieve user email addresses, names, and phone numbers. This flaw exposed sensitive information in the API response, even though it was not visible to users during the login process.
2.2 Discovery and Notification
The breach was initially reported by HackManac and later confirmed by BleepingComputer, which verified the legitimacy of the leaked data. Life360 subsequently acknowledged the breach and disclosed that the API flaw had been fixed.
2.3 Public Disclosure
The attacker, emo, publicly revealed the breach and shared details about the exploit method. Along with the Life360 breach, emo also leaked more than 15 million email addresses linked to Trello accounts, which were obtained through a similarly unsecured API.
3. Root Cause Analysis
3.1 Vulnerability Exploited
The breach resulted from an unprotected API endpoint in the Life360 login system. This endpoint exposed sensitive information, such as first names and phone numbers, during the login process. As a result, the attacker could effortlessly verify and extract user data.Top of FormBottom of Form
3.2 Security Oversight
The vulnerability in the API endpoint indicates a failure in Life360's security protocols. The lack of proper input validation and security checks allowed the attacker to exploit the flaw and collect a significant amount of user data undetected.
4. Exploit Method
Step-by-Step Technique Used by the Attacker
-
Identification of Unsecured API Endpoint:
-
The attacker discovered a vulnerable API endpoint in the Life360 login system that revealed sensitive user information in its responses.Top of FormBottom of Form
-
Data Scraping:
-
The attacker employed automated scripts to send login requests to the API endpoint, with each request revealing the user's first name and phone number.
-
For users who had verified their phone numbers, the API returned a partial number (e.g., +1******4830).
-
Verification of User Data:
-
The attacker cross-checked the returned data against known email addresses to confirm the validity of the information.
-
This process enabled the attacker to assemble a database containing 442,519 Life360 customers.
-
Public Disclosure:
-
The attacker, Emo, made the breach public and detailed the method used to exploit the API vulnerability.
-
Additional leaks included over 15 million email addresses from Trello, collected using a similar method.
Technical Breakdown of the Exploit
-
API Endpoint Flaw: The login API endpoint exposed sensitive user information, such as first names and phone numbers, in its responses to login attempts. This data was included in the API response and was not visible to users.
-
Lack of Input Validation: The API did not adequately validate input or limit the type and amount of data returned in the response.
-
Absence of Rate Limiting: There was no rate limiting on the API endpoint, allowing the attacker to send a high volume of requests and collect a large amount of data in a short period.
-
Automation: The attacker used automated scripts to systematically send requests to the API endpoint and scrape the returned data.
5. Conclusion
The Life360 data breach highlights critical vulnerabilities in the company's API security infrastructure. The breach was facilitated by inadequate security measures in the login API and a lack of effective monitoring and detection systems. Life360's prompt response and communication were necessary steps, but the incident underscores the need for more robust security practices.
Recommendations
To prevent future breaches, Life360 should implement the following measures:
-
Strengthen API Security Protocols: Enhance security measures in online portals, including rate limiting, two-factor authentication, and regular security audits for APIs.
-
Improve Monitoring Systems: Deploy advanced anomaly detection systems to identify unusual API activity in real-time.
-
Enhance Incident Response: Establish a more responsive incident management framework to quickly address vulnerabilities and breaches.
-
Transparent Communication: Adopt a more transparent approach in communicating with customers and stakeholders during and after security incidents.
By addressing these areas, Life360 can improve its security posture, restore customer confidence, and mitigate the risk of future data breaches.
In today's digital landscape, ensuring the security of APIs is crucial to safeguarding sensitive information and preventing data breaches. The Life360 data breach underscores the critical importance of robust API security measures. To prevent such incidents in the future, it is essential to adopt comprehensive security practices and leverage advanced tools like APIFUZZER™, an API testing solution designed to enhance API security by detecting vulnerabilities in the pre-production environment.
How APIFUZZER™ Can Help
-
Pre-Production Vulnerability Detection: APIFUZZER™ excels at identifying vulnerabilities before APIs go live, ensuring that potential security issues are addressed in the pre-production environment. This proactive approach minimizes the risk of data breaches and ensures that APIs are secure before they are exposed to real-world traffic. APIFUZZER™ has capability to discover the exposure of sensitive data, Personal information, excessive data and more by APIs and provides mitigation techniques with code snippets.
-
API Discovery: APIFUZZER™ helps you discover all the APIs in use, providing a comprehensive overview of your API landscape. This visibility is crucial for maintaining control over your API environment and ensuring that no endpoints are left unmonitored. APIFUZZER™ then helps you create your API-SBOM which helps you to create your application API Inventory.
-
Security Vulnerability Scanning: Once the APIs are identified, Rapiuzz scans them for security vulnerabilities, ensuring thorough protection against potential threats. This includes testing for common vulnerabilities like unsecured data exposure and improper input validation.
-
Smart Fuzzing Technique: APIFUZZER™ employs a smart fuzzing technique that aggressively scans and tests your APIs for vulnerabilities, providing a robust assessment of your API security posture. This technique simulates real-world attack scenarios, identifying weaknesses that could be exploited by threat actors.
-
Compliance with OWASP Standards: APIFUZZER™ adheres to OWASP API Security standards for 2019 and 2023, ensuring that your APIs are evaluated against the latest security guidelines. This compliance guarantees that your APIs meet industry best practices for security.
-
Best Practices for API Security: APIFUZZER™ not only detects vulnerabilities but also suggests best practices for enhancing API security, helping you implement effective measures to safeguard your systems.
-
Project Compare: In a security testing environment, it is important for organizations to test the application again for vulnerabilities and ensure that in the process of mitigating the vulnerability no new vulnerabilities have been introduced and if there are any deprecated APIs which have slipped past into the AUT. Our compare function helps organizations to discover deprecated APIs and ensure a stronger product.
APIFUZZER™ has additional features and is DevSecOps ready and can ensure your organization's APIs are secure before they reach production, significantly reducing the risk of data breaches and enhancing your overall security posture. By implementing APIFUZZER™, organizations like Life360 can proactively identify and mitigate API vulnerabilities, thereby enhancing their overall security posture and protecting sensitive user data from malicious actors.