Brute Force & Vulnerable APIs: How Dell-like Breaches Could Be Prevented
Text to Speech in Multiple Languages
Recently, Dell faced a major data breach, compromising the personal information of around 49 million customers. Initially reported by Daily Dark Web, threat actor Menelik orchestrated the breach and tried to sell the Dell database on the hacking platform called Breach Forums. TechCrunch confirmed the legitimacy of the data by verifying it against actual Dell customer records.
Menelik was able to brute-force the portal to scrape customer data, including names, physical addresses, and order information. This blog examines the
- details of the incident.
- response actions taken by Dell.
- root cause analysis.
- impact of the breach.
- recommendations for prevention of incidents.
Incident Details
The attacker gained access to Dell's customer data by registering as a partner and leveraging brute force techniques to obtain service tags associated with customer accounts through vulnerable APIs. Over a period of nearly three weeks, Menelik sent approximately 50 million requests to Dell's server, eventually scraping data for around 49 million customers, as reported by TechCrunch and Ars Technica.
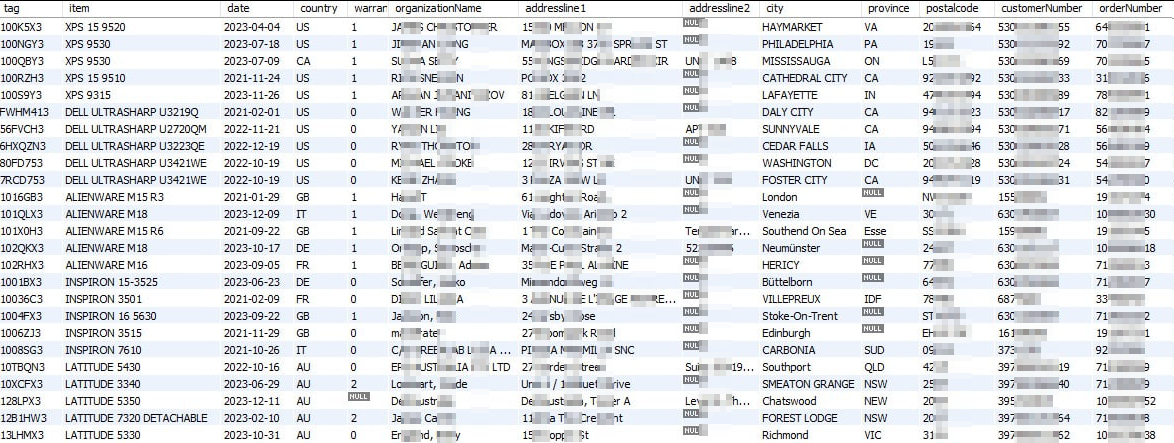
Image courtesy: Daily Dark Web
Discovery and Notification
Dell was informed of the breach by the attacker, who sent multiple emails to Dell, notifying the company of the vulnerability and the ongoing data scraping. Despite receiving this notification, it took Dell almost a week to patch the API vulnerability. Dell subsequently informed customers of the breach via email, attempting to downplay the significance by suggesting the exposed data was not highly sensitive.
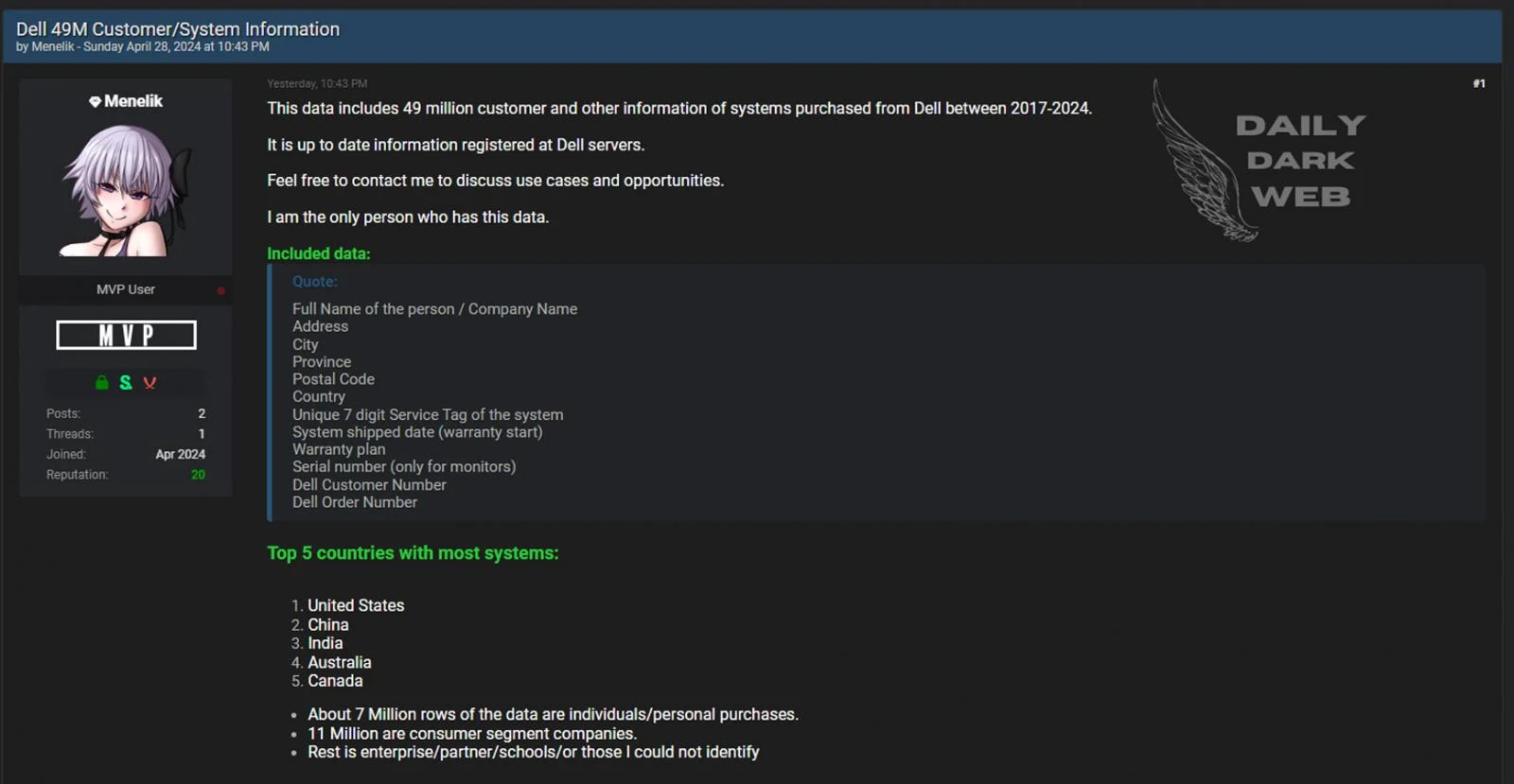
Image courtesy: Daily Dark Web
The screenshot above shows that the Dell data breach exposed detailed customer records, including names, addresses, and unique identifiers like service tags and warranty information. This comprehensive set of personal and system information was compromised and allegedly put up for sale on the dark web, illustrating the gravity of the breach. Such detailed information can be used for identity theft, targeted scams, and other malicious activities, emphasizing the urgent need for strong cybersecurity measures.
Technical Breakdown of the Exploit
- Service Tags Structure: The service tags were seven characters long, containing only numbers and consonants, which reduced the complexity and increased the feasibility of brute-forcing.
- API Endpoints: The specific API endpoints did not have adequate security measures, such as rate limiting, which would have prevented high-frequency requests.
- Lack of Detection: The API lacked robust anomaly detection mechanisms to identify and flag unusual patterns of activity, such as the high volume of requests being generated by the attacker.
- Rate Limiting Absence: The absence of rate limiting allowed the attacker to send more than 5,000 requests per minute without triggering any security alerts.
Root Cause Analysis
The root cause of the breach was a vulnerability in Dell's online partner portal APIs. These APIs, intended for use by resellers, retailers, and partners of Dell products and services, allowed the attacker to register multiple accounts without verification, brute-force data, and make an extensive number of requests.
Security Oversight
The prolonged period during which the attacker was able to scrape data indicates a loophole in Dell’s security monitoring and response protocols. The absence of real-time detection mechanisms enabled the attacker to operate undetected for nearly three weeks.
API Security Recommendations
The Dell data breach incident underscores the critical importance of robust API security in protecting sensitive customer information. As demonstrated, threat actors like Menelik can exploit vulnerabilities in API endpoints, leading to significant data breaches and compromising millions of customer records. Such incidents underscore the importance for organizations to focus on strengthening their API security protocols.
Incorporating insights from sources like OWASP API Security Top 10 provides a comprehensive view of API security risks and how they can be exploited. To prevent future breaches, organizations should implement the following measures:
- Strengthen API Security Protocols: Enhance security measures in online portals, including rate limiting, two-factor authentication, and regular security audits for APIs.
- Improve Monitoring Systems: Deploy advanced anomaly detection systems to identify unusual API activity in real time.
- Enhance Incident Response: Establish a more responsive incident management framework to quickly address vulnerabilities and breaches.
- Transparent Communication: Adopt a more transparent approach to communicating with customers and stakeholders during and after security incidents.
APIFUZZER™ emerges as a vital tool in this context, offering advanced API security testing capabilities that help organizations uncover and mitigate vulnerabilities. APIFUZZER™ is a clientless DevSecOps solution which can allow you to test your APIs for ‘Rate Limiting’, and has a number of unique test cases without you having to deploy a API gateway. By simulating various attack scenarios for ‘Rate Limiting’, and using fuzz testing, APIFUZZER™ can help you discover these unknown vulnerabilities and provide you detailed mitigation methods. Apart from the available mitigation methods our experienced API security experts can guide development teams to fix these vulnerabilities in a short period of time. Its customizable settings allow for tailored security measures, including sophisticated rate limiting strategies, ensuring APIs are both secure and efficient.
Why APIFUZZER™?
- Comprehensive Security: APIFUZZER™ offers extensive testing capabilities that help organizations identify and mitigate vulnerabilities that could lead to breaches similar to the Dell incident.
- Customization and Control: Users can set specific parameters for their testing needs, such as rate limits and burst limits, ensuring tailored security measures that align with their system's capacity and usage patterns.
- Advanced Handling of Rate Limits: APIFUZZER™ allows organizations to implement sophisticated rate limiting strategies, providing tools to manage how often users can make requests, thereby preventing abuse and ensuring stable API performance.
Leveraging advanced API security platforms like APIFUZZER™ is essential for safeguarding digital assets. By implementing these robust security measures, organizations can enhance their security posture, restore customer confidence, significantly reduce the risk of future data breaches, and ensure a secure and efficient user experience. For further information on how APIFUZZER™ can bolster your API security, visit APIFUZZER™