Understanding the Role of Red Teams in Cybersecurity
Text to Speech in Multiple Languages
Think of red teams as the fire drills of cybersecurity: just as fire drills prepare us for emergencies without the actual danger, red teams simulate cyber-attacks to test an organization’s defences in a safe environment. They play a crucial role in an enterprise’s cybersecurity framework by acting as ethical hackers who identify weaknesses in IT systems.
In this blog, we will explore what red teams are, their purpose, the different types, and how they collaborate with blue and purple teams to strengthen organizational security. We’ll also discuss the benefits of red teaming, real-world examples of how it has helped organizations, and the effectiveness of this strategy in addressing various threats.
What Is a Red Team in Cybersecurity?
A “red team” is a group of cybersecurity professionals who simulate attacks against an organization’s IT defences. Red teams adopt the role of malicious actors, using tools and techniques common among cybercriminals to breach the security of the IT environment. They typically have various roles, including team leader, penetration tester, social engineer, and specialists in areas such as network security, application security, and physical security.
- Purpose of a Red Team: The primary goal of a red team is to evaluate a company’s IT security posture without exposing it to risk from actual threat actors. By conducting authorized, controlled “attacks” on an IT environment, red teams help organizations identify security flaws and make recommendations for resolving these vulnerabilities before they can be exploited.
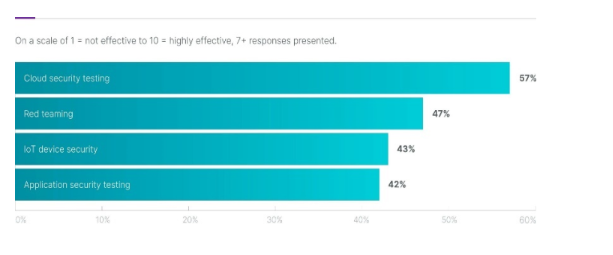
The Effectiveness of Red Teaming
Red Teaming is recognized as the second most effective offensive security testing strategy, with 47% of organizations citing its effectiveness, just behind cloud security testing at 57%, according to the 2023 Ponemon Institute Report: The State of Offensive Security. Tailored to simulate specific threat actors, tactics, and scenarios, Red Teaming delivers a strong return on investment (ROI) against a wide array of threats. Depending on an organization’s needs, Red Teaming can assess ransomware readiness, simulate insider threats, and evaluate a Blue Team’s capacity to detect and respond to particular malware types, among other scenarios.
Different Types of Red Teams
Red teams come in various forms, which can be distinguished by:
-
Internal/External: Red teams may consist of internal employees, external security consultants, or a combination of both.
-
Attack Scenario: Red teams can be “adversarial,” meaning they have limited information about the target, simulating a real attacker’s perspective. Alternatively, they may work cooperatively with the target during the simulat
What Are Red Team Exercises?
Red team exercises (or “red teaming”) are simulations designed to assess an organization’s IT security structure by placing it under stress or attack. The primary objective is to identify and resolve vulnerabilities that malicious actors could exploit.
The Process of Red Teaming
Red teaming typically involves several stages:
- Defining the Scope: Determine specific targets for the engagement.
- Intelligence Gathering: Collect intelligence and perform reconnaissance to identify effective attack methods.
- Attack Planning: Create a plan outlining tools and techniques to be used.
- Controlled Attacks: Execute a series of controlled attacks on the target, including vulnerability scanning and social engineering.
- Analysis and Recommendations: Evaluate the results of the attacks and recommend improvements for IT security.
Different Red Team Exercises
Examples of red team exercises include:
- Network Penetration Tests: Exploiting weaknesses in networks and devices, such as misconfigurations.
- Social Engineering Tests: Tricking employees into divulging confidential information.
- Web Application Tests: Exploiting vulnerabilities like SQL injection and cross-site scripting (XSS).
- Physical Security Tests: Gaining physical access to secure areas, such as server rooms.
Benefits of Red Teaming
The key advantages of red teaming include:
- Identifying Vulnerabilities: Simulating the mindset of malicious actors helps organizations detect weaknesses without falling victim to real cyber-attacks.
- Evaluating Incident Response: Red teams strengthen the capabilities of blue teams by assessing the effectiveness of detection and incident response measures.
- Awareness and Compliance: Red team exercises raise awareness of IT security across the organization and help demonstrate compliance with data security regulations.
Tools Used by the Red Team
Common tools in red teaming exercises include:
- Data Collection and Reconnaissance Tools: Such as open-source intelligence (OSINT).
- Network Scanning Tools: Like Nmap and MASSCAN, which map out the target’s network infrastructure.
- Exploitation Frameworks: Tools like Metasploit that help identify vulnerabilities.
- Password Cracking Tools: Used to attempt unauthorized access to IT systems.
Conclusion
Red teaming is a vital practice for organizations of all sizes and industries to evaluate and enhance their IT security. As businesses increasingly focus on defending against cyber threats, the role of red team members remains dynamic and critical. By proactively identifying vulnerabilities and improving incident response capabilities, red teams empower organizations to fortify their defences against the ever-evolving landscape of cyber threats.
Platforms like CYBERKSHETRA™ further strengthen these efforts by providing an immersive training environment that replicates real-world cyber threats. Through realistic simulations and complex scenarios, CYBERKSHETRA™ equips cybersecurity professionals with practical skills and insights essential for effectively addressing a wide range of challenges. It offers advanced tools and techniques for hands-on learning, enabling users to refine their abilities in a controlled setting.
Additionally, CYBERKSHETRA™ seamlessly integrates with all stages of the DevSecOps process, fostering collaboration between development and security teams. By enhancing the training experience and supporting the continuous development of red teams, CYBERKSHETRA™ helps organizations ensure they are well-prepared to counteract the persistent threat of cyber-attacks. Together, red teaming and innovative training solutions like CYBERKSHETRA™ create a robust defence strategy, reinforcing organizational resilience in an increasingly digital landscape.