.png)
API Discovery
In our increasingly interconnected digital world, APIs (Application Programming Interfaces) serve as the conduits that facilitate communication between various software components. Comprehensive API discovery is the first step in harnessing their potential. With our solution, Organizations can create a detailed list of their API Inventory or the API-SBOM
- Enabling developers to validate their API documentation and assisting integration of your applications with other/third-party applications
- Security professionals to assess the security of exposed APIs
- Compliance teams to validate if their APIs comply with industry standards and regulatory requirements.
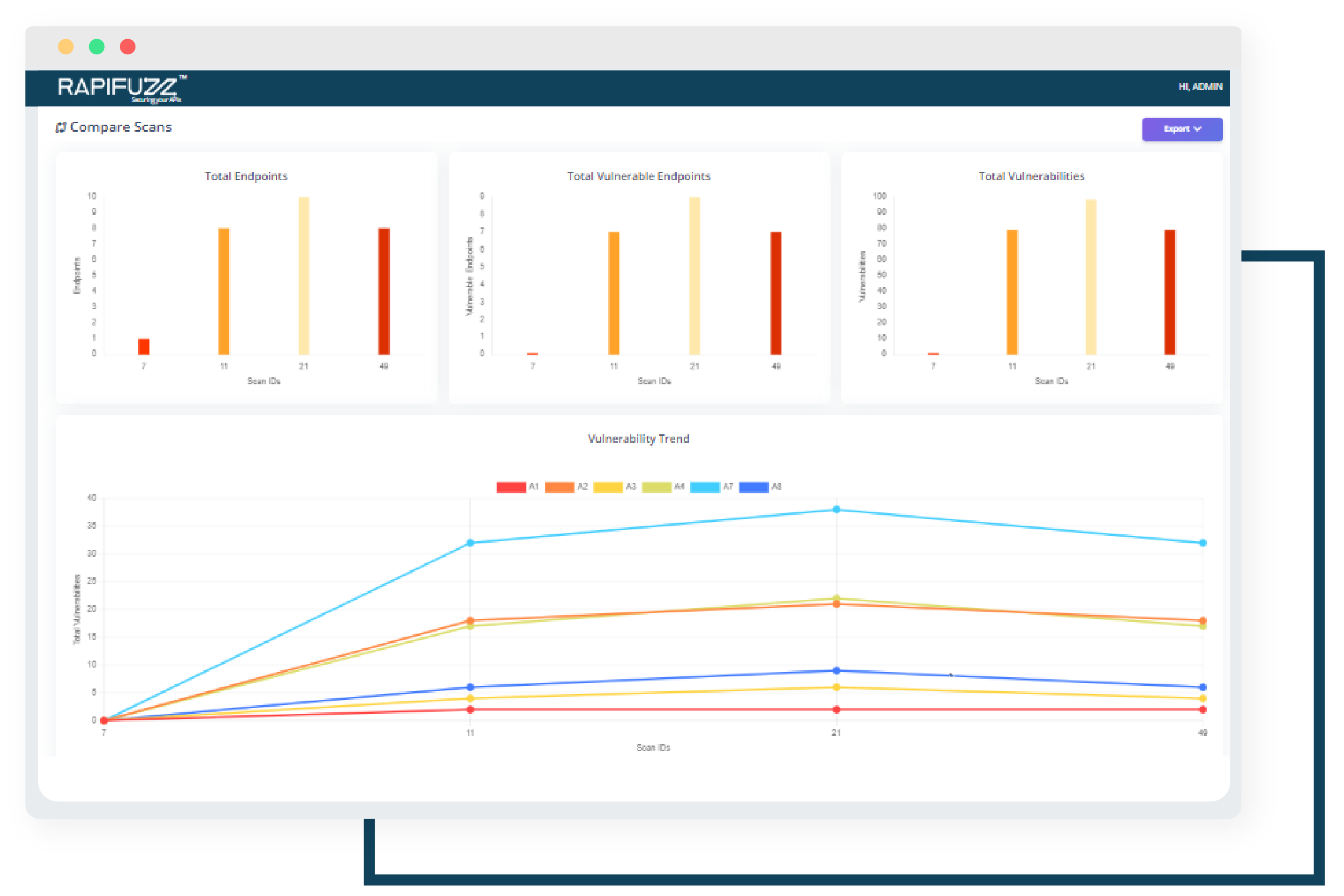
API Lifecycle & ROI
The API Lifecycle represents the various stages an API goes through from its initial concept to its retirement or replacement. It is important to be able to compare different versions of your application to see the vulnerability trends across APIs and applications and how the solution has helped you reduce your risks and ascertain areas of improvement.
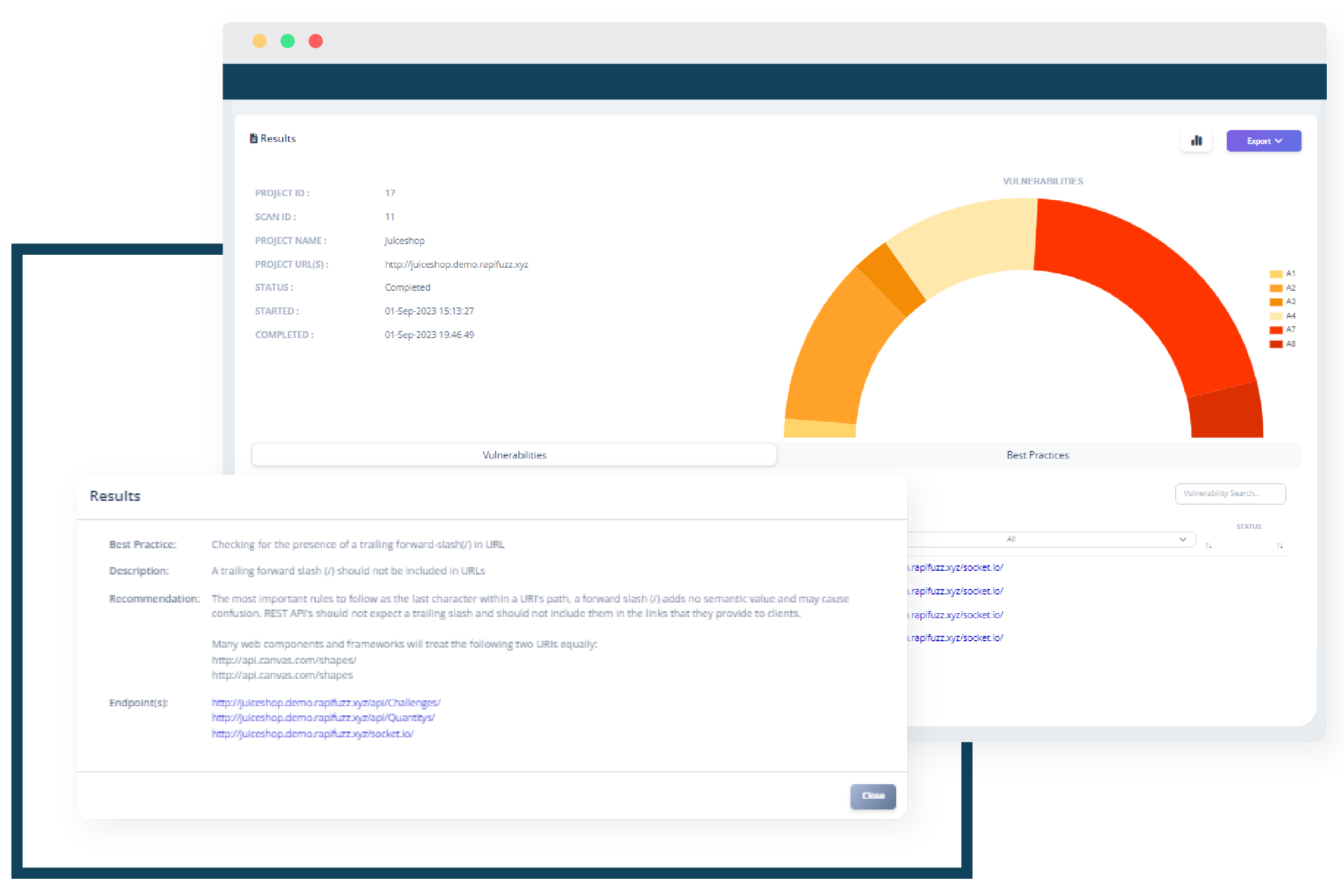
API Security Best Practices
Checking APIs for best practices is essential for several reasons, as it helps ensure the reliability, security, and efficiency of APIs in various contexts. Our use cases check for different best practices for RestAPIs like encryption algorithms used, rate limiting, error handling, etc.
Broken User Authentication
A Broken User Authentication attack is a type of cybersecurity threat that exploits vulnerabilities in the authentication process of a web application or system, allowing attackers to gain unauthorized access to user accounts, sensitive data, or system resources. This type of attack typically occurs when there are weaknesses or flaws in how user authentication is implemented, verified, or managed within an application.

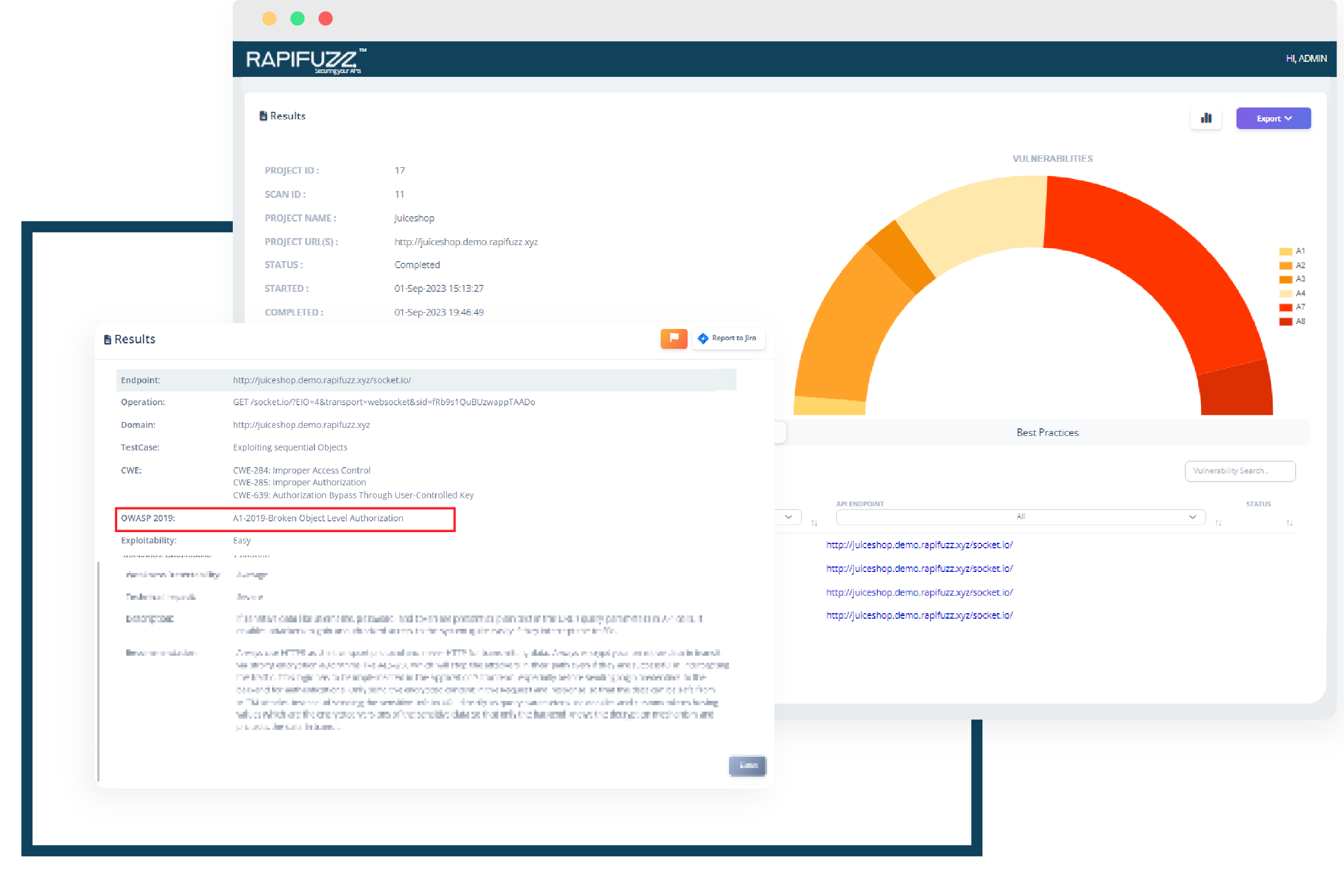
Broken Object-level Authorization
A Broken Object-Level Authorization (BOLA) attack, sometimes also referred to as an Insecure Direct Object Reference (IDOR) attack, is a type of security vulnerability in web applications. In a BOLA attack, an attacker manipulates input to access or modify objects (such as files, database records, or resources) that they are not authorized to access. This typically occurs when the application does not properly enforce or validate user permissions, relying solely on user input to determine access to objects.
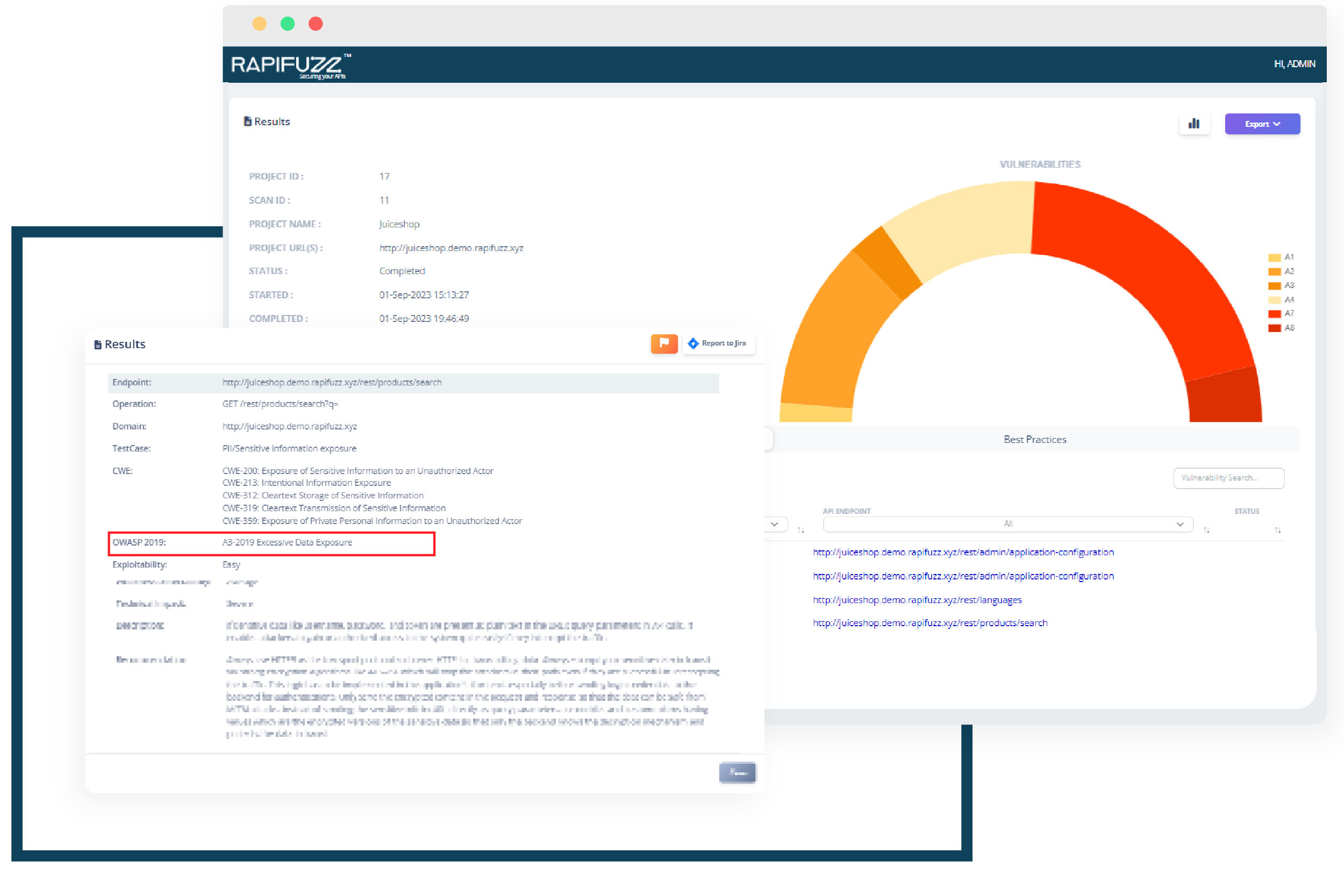
Excessive Data Exposure
Excessive Data Exposure refers to a cybersecurity issue where an application, system, or service inadvertently or unnecessarily exposes more information than is required or intended to be made available to users or the public. It occurs when sensitive or confidential data is disclosed without proper access controls or privacy safeguards, potentially putting the data and individuals' privacy at risk.
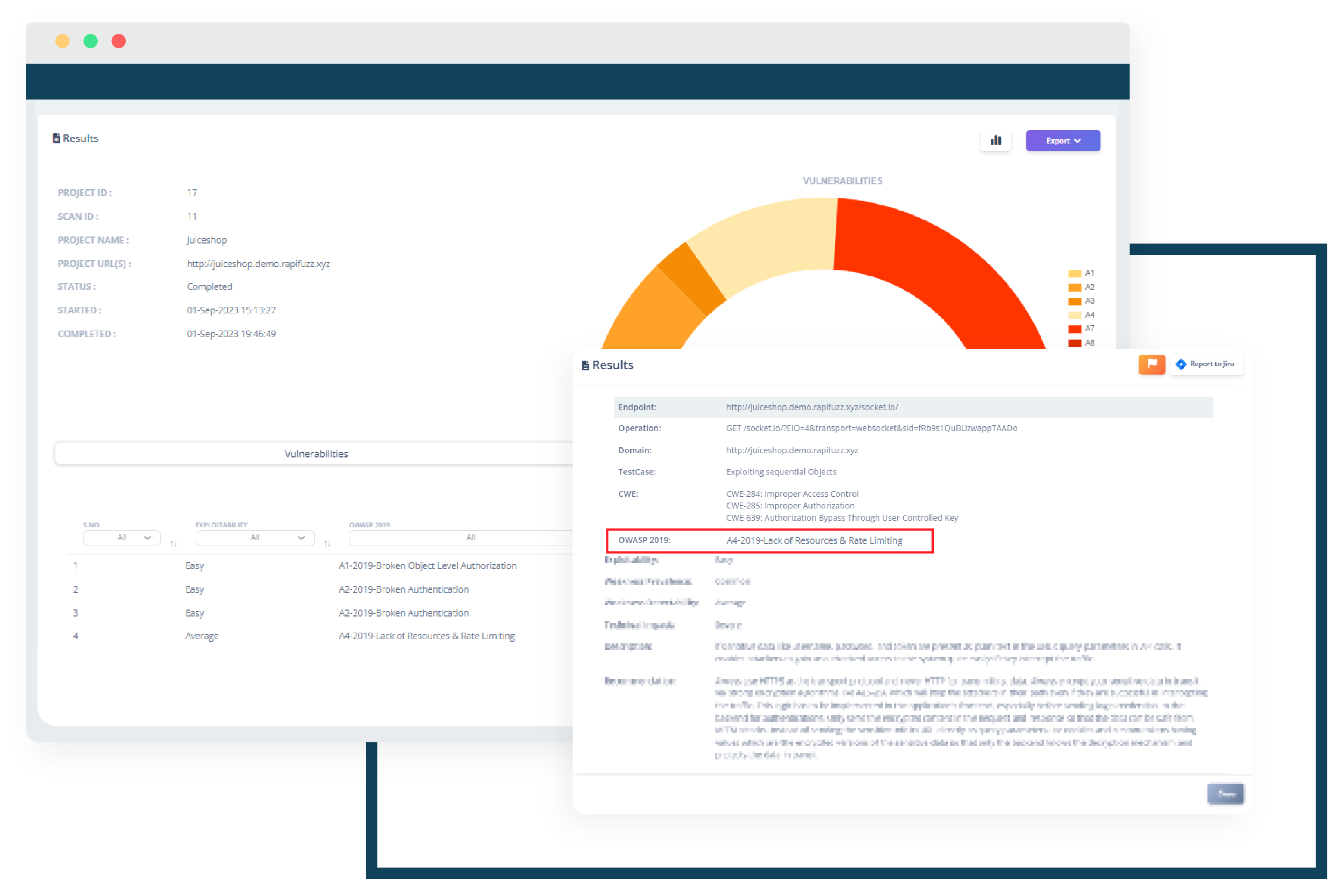
Lack of Resources and Rate Limiting
"Lack of Resources" pertains to insufficient system resources to handle workloads effectively, while "Rate Limiting" is a control mechanism used to restrict the rate or frequency of API requests to maintain service quality and prevent misuse or overload. Both concepts are essential for ensuring the reliability and performance of APIs and web services.
Broken Function Level Authorization
Attackers send legitimate API calls to the API endpoint that they should not have access to. These endpoints might be exposed to anonymous users or regular, non-privileged users. allowing an attacker to gain unauthorized access to functionality or data.

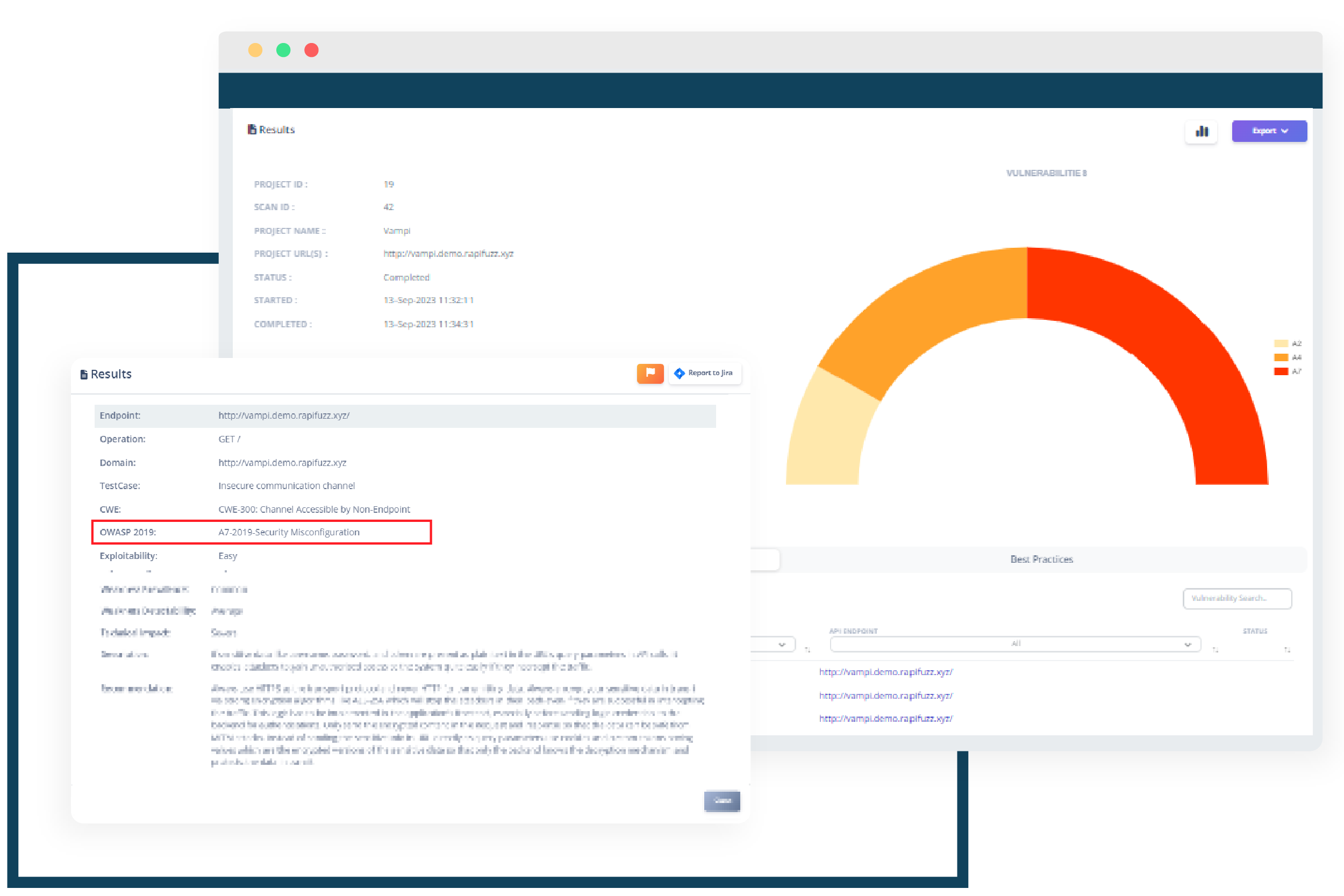
Security Misconfiguration
A Security Misconfiguration attack is a type of cybersecurity threat that occurs when a system, application, or network is configured or set up in a way that inadvertently exposes security vulnerabilities. It is a common type of attack that takes advantage of mistakes or oversights made by administrators or developers during the configuration process. These misconfigurations can create security weaknesses that malicious actors can exploit.
Injection
Injection attacks are a category of cybersecurity threats in which malicious code or data is injected into an application or system, causing it to behave unexpectedly or execute unauthorized actions. These attacks typically occur when an application or system processes untrusted input from users or external sources without proper validation or sanitization. Injection attacks can lead to data breaches, system compromise, and various security vulnerabilities.

